# Topic covered
AWS Infrastructure
AWS Regions are separate geographic areas that AWS uses to house its infrastructure. Now has 31 Regions
# Example
* Mumbai (ap-south-1)
* Hong Kong (ap-east-1)
* Singapore (ap-southeast-1)
Availability Zones(AZs): Each region has multiple AZs and when you design your infrastructure to have backups of data in other AZs,
Now has 99 Availability Zones.
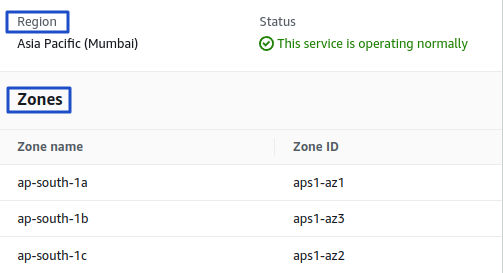
For Mumbai (ap-south-1) Region by default we have following AZs
# EC2 Dashboard
* ap-south-1a (aps1-az1)
* ap-south-1b (aps1-az3)
* ap-south-1c (aps1-az2)
Edge Location is the Data Center used to deliver content fast to your users. It is the site that is nearest your users.
- Eg: CloudFront uses to cache copies of your content for faster delivery to users at any location.
Local Zones are designed to bring the core services needed for the latency sensitive portions of your workload closer to end-users, while Availability Zones provide access to the full array of AWS services.
NOTE
Every region is physically isolated from and independent of each other in terms of location, power, water supply, etc.
but the AZs within each region are connected via low-latency links to provide replication and fault tolerance.
- Resource in region-1 is not visible in region-2
- EC2 running in region-1 is not visible in other region
- So
be causionabout your region
What is IAM?
Identity Access Management- IAM allows you to manage users and their level of access to the AWS console.
- In simple give access to different users/machines to the same AWS account
- It is a
Global service, not specific to any AWS Region
Securing root account
- Enable
Multi-factor authenticationfor root userAuthenticator appinstalled on your mobile device or computer
- Never generate
root level key-pairs(Access keys and Cloudfront Keys)
Features of IAM
- Centralised control of your AWS account
- Shared Access to your AWS account
- Permissions based on Organizational groups
IAM Identities
- IAM Users
- IAM Groups
- IAM Roles
Users
- An
IAM useris an identity with long-term credentials that is used to interact with AWS in an account. -
IAM > Access management > Users
# Create users
Name: User1
Credential type:
1. Programmatic access
* Enables an access key ID and secret access key
* For the AWS API, CLI, SDK, and other development tools
2. AWS Management Console access
* Enables a password
* That allows users to sign in to the AWS Management Console.
Create account alias-
IAM > Account alias > create
- Now can use Account Alias instead of Account ID for login
-
Note:Never copy permissionsfrom an existing user, Just add users to Groups- After successful user creation –>
Download key-pairs- Because - it’s only one time accessible
Users groups
- A user group(
IAM Groups) is acollection of IAM users - Different Groups have different types of permissions
- We create our own IAM groups like:
- Admin, Developer, Tester, etc
- Any user added to the group, Will all the permission be given to the Group
-
IAM > Access management > User groups
# Create Admin Group - Use this
Name: MyAdmin
Policies: AdministratorAccess
* Provides full access to AWS services and resources on
* "Action": "*",
* "Resource": "*"
# Don't use - has limitation
* Policies: SystemAdministrator
* Grants full access permissions on necessary for resources
* that are required for application and development operations.
# Create Dev Group
Name: MyDev
Policies: AmazonEC2FullAccess
Roles
- An IAM role is similar to an IAM user, but it is generally
used by machines/services - Want to run an resourses that also needs other resources then AWS creats a role
- Also used as Temporary security credentials in IAM
- Role can only be used in EC2 instance
- IAM > Access management > Roles > create-roles > add-permissions
- Open-EC2-instance > Actions > Security > Modify IAM role > select-the-role-to-apply
Create Billing Alert
- Useful to monitor your usage, and analyze and
control your costs - Trun on Billing Alerts
-
Billing Dashboard > Preferences > Billing Preferences
- Receive PDF Invoice By Email
- Receive Free Tier Usage Alerts
- Receive Billing Alerts
-
Alert can be set in two ways
- Manage Billing Alerts
-
CloudWatch > Alarms > Billing > Create alarm
- Define the threshold value
- Alarm state trigger
- Create topic or select existing
- Add name, description and Create
- Confirm SNS email subscription by clicking on conformation email-link
- The new budgets feature!
-
Billing Dashboard > Cost Management > Budget > Create Budget
- Cost budget - Recommended
- Works for 80%-90%
-
Password Compliance
- A password policy is a set of rules that define complexity requirements and mandatory rotation periods for your IAM users' passwords.
- IAM > Account Seting > Change password policy